Trézor Login | Desktop & Web App for Hardware
A Secure and User-Friendly Access Experience (Presentation Content)
Introduction
In the rapidly evolving world of digital finance, security is a top priority. Hardware wallets have become one of the most trusted solutions for safeguarding cryptocurrencies and digital assets. Among these, Trezor stands out as a pioneer in the hardware wallet industry. This presentation explains the Trezor hardware login process, highlighting how it works, why it is secure, and what users should know to log in safely and confidently.
What Is a Trezor Hardware Wallet?
A Trezor hardware wallet is a physical device designed to store private keys offline. Unlike software wallets, which remain connected to the internet, Trezor keeps sensitive cryptographic data isolated from online threats. Logging in with a Trezor wallet does not mean entering credentials on a website; instead, it involves verifying identity directly on the hardware device itself.
Why the Login Process Matters
The login process is the first line of defense against unauthorized access. Trezor’s login mechanism is built around three key principles:
- Offline security – Private keys never leave the device
- User verification – Physical confirmation is required
- Phishing resistance – No passwords are typed into browsers
This approach significantly reduces the risk of hacking, malware attacks, and credential theft.
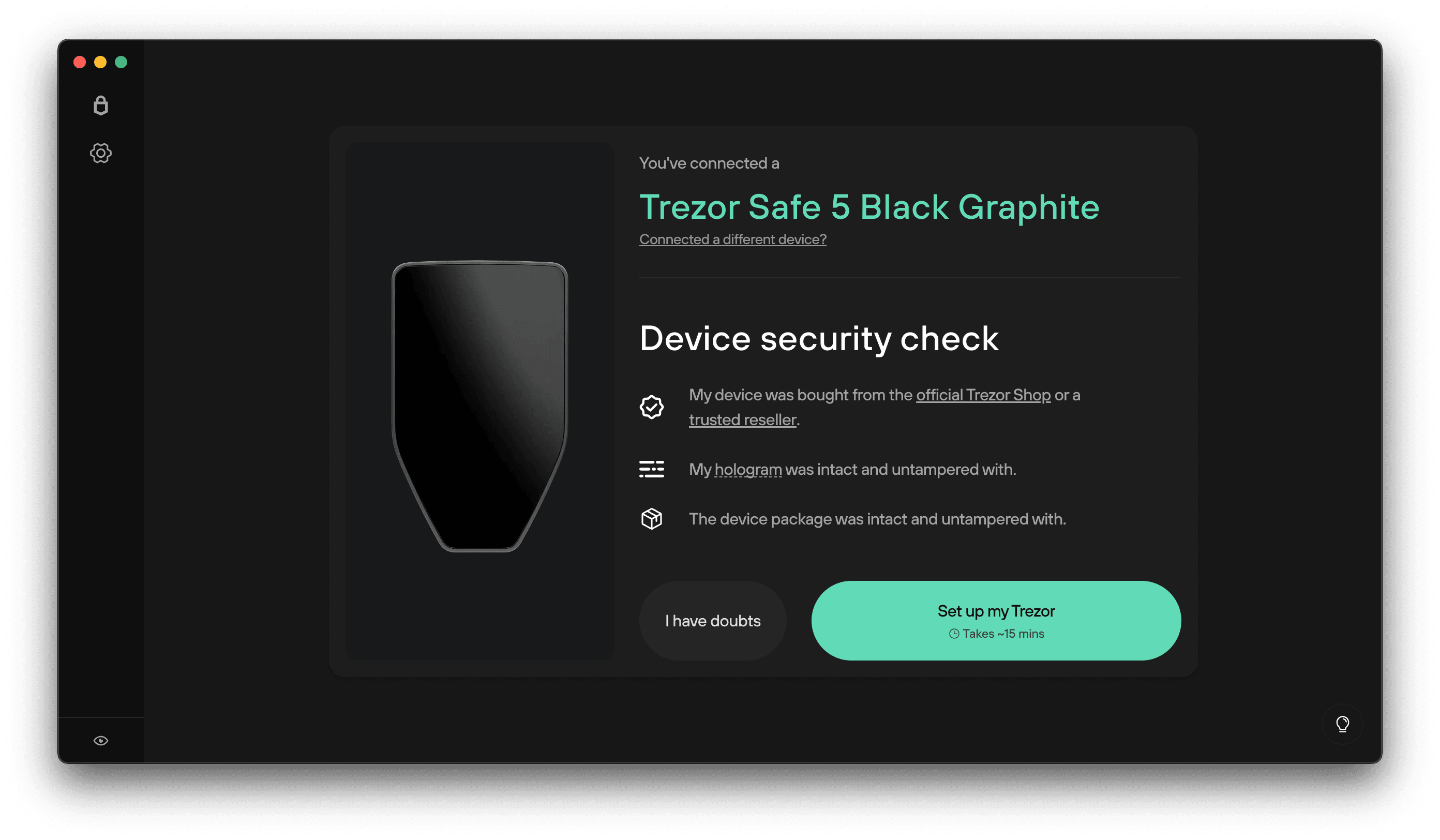
Trezor Login Overview
Logging into a Trezor wallet is typically done through the official desktop or web interface provided by the company. The process includes connecting the device, verifying identity using a PIN or passphrase, and confirming actions on the hardware screen.
High-Level Login Flow
- Connect the Trezor device to a computer or mobile device
- Open the official Trezor interface
- Enter the PIN using a randomized keypad
- Confirm login on the hardware device
- Access wallet accounts securely
Visual Overview of the Login Experience


4
Step-by-Step Login Explanation
1. Connecting the Device
The user begins by physically connecting the Trezor hardware wallet via USB. This step ensures that login cannot occur remotely. Without the physical device, access is impossible.
2. Launching the Official Interface
Once connected, the user opens the official Trezor application on their computer or supported browser. This software acts as a bridge, allowing communication with the hardware wallet without exposing sensitive data.
3. PIN Verification
The PIN is a critical part of the login process. Instead of typing numbers directly, Trezor displays a randomized keypad on the computer screen while the actual numbers appear only on the device. This prevents keyloggers and screen-capture malware from stealing the PIN.
4. Device Confirmation
After entering the correct PIN, the device requests confirmation. This ensures the user is physically present and aware of the login attempt. Any unauthorized attempt is immediately blocked.
5. Wallet Access
Once verified, the wallet interface unlocks, allowing the user to view balances, send transactions, or manage accounts—while private keys remain securely offline.
Optional Security Layer: Passphrase
For advanced users, Trezor offers an optional passphrase feature. This acts as an additional “hidden wallet” layer. Even if someone knows the PIN, they cannot access funds without the passphrase. Each unique passphrase creates a separate wallet, providing strong protection against coercion or theft.
Key Security Benefits of Trezor Login
- No online passwords to steal
- Physical device requirement for every login
- Protection against phishing websites
- Secure recovery system using a recovery seed
- Transparent, open-source security model
Common Login Issues and Solutions
- Forgotten PIN: Reset the device and recover funds using the recovery seed
- Device not detected: Check USB cable, drivers, or try another port
- Wrong interface: Always use the official Trezor software to avoid scams
Best Practices for Safe Login
- Always verify the website or application source
- Never share your recovery seed or passphrase
- Store the recovery seed offline in a secure location
- Keep the device firmware up to date
- Avoid using public or untrusted computers
Conclusion
The Trezor hardware login process is designed to balance maximum security with ease of use. By combining physical verification, randomized PIN entry, and offline key storage, Trezor ensures that users maintain full control over their digital assets. Whether you are a beginner or an experienced crypto holder, understanding the login process is essential to maintaining strong security and peace of mind.